We Bought All These Cybersecurity Tools. Now What?
In recent years, companies have acquired large numbers of cybersecurity tools to combat the evolving threat landscape. Hackers have become more sophisticated – and companies are throwing money at security products and solutions to prevent the kinds of attacks they hear most frequently reported in the news.
A few trends have converged. For one, the increased number of remote workers has driven significant change in the way companies manage end-user devices. This has forced basic anti-virus solutions to become managed detection and response (MDR) platforms. Companies of all sizes and industries have had to adopt vulnerability scanners for basic infrastructure and applications. Enterprise adoption of complex network technologies like SD-WAN and SD-LAN and the migration of workloads to the cloud have further complicated the way companies manage their security stacks. Many have chosen to quickly adopt SASE, XDR, CASB and other “solutions” too numerous to name. Sitting underneath all this is a hornet’s nest of identity governance.
Research indicates the proliferation of tools to improve cybersecurity is consuming a large portion of security budgets and will continue to grow. Enterprise spend on cybersecurity tools and technologies will likely account for more than a staggering $100 billion by 2024.
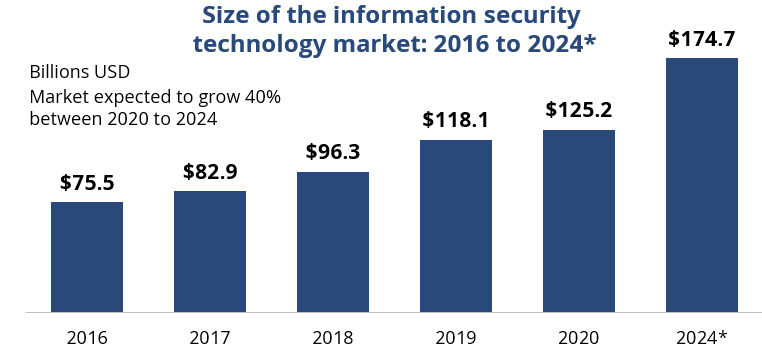
Source: Statista. 2021. Used with Permission
Despite these investments, companies continue to experience security incidents at an alarming rate. We believe this is because of a failure to properly define, implement and execute a closed loop compliance process.
Cybersecurity Compliance Challenges
As organizations accelerate their digital transformation initiatives and move more and more workloads to the cloud, a considerable gap is emerging in compliance. The pace of change that accompanies the adoption of Agile practices is compounding the issue. When IT organizations neglect the basic blocking and tackling necessary for robust compliance, they often face increased risk of a security breach. Vulnerability management programs are only as good as the processes in place for granting, documenting and continually reviewing exceptions to patching policies.
Many companies struggle to minimize exceptions. For example, product teams often refuse to clean up their code due to pressures to meet development and allow exceptions to linger indefinitely. Another common scenario for excessive exceptions is when plant floor managers try to balance just-in-time manufacturing and delivery with contracted service targets and required maintenance windows.
Compounding the issue is a lack of enterprise focus on resiliency and the need to recover quickly in the event of a serious incident.
Assess Your Compliance Capabilities
To be sure, investing in tools is a component of the compliance lifecycle. However, we routinely see companies that omit the continuous review portion of the cycle and suffer from poor hygiene, leading to breaches that are entirely preventable. This problem seems particularly onerous in organizations that have adopted a multi-provider model for delivery of IT services, with providers minimizing efforts to achieve compliance and limiting accountability for platforms under their control. In the past 18 months we have seen many CISO organizations struggle with this issue.
ISG can help you identify compliance issues and gaps in service delivery models. We help enterprises improve their compliance programs in three steps:
- Analyze security operating models, vulnerability management and compliance programs.
- Leverage best-practice IP and ISG’s contracts database to rapidly address immediate compliance gaps and help implement a closed-loop compliance process.
- Develop a strategic roadmap that aligns compliance functions with the CISO’s mandate, ensuring a cohesive compliance program across all platforms and providers in the ecosystem.
Contact us to find out how we can help you assess where you are today and where you need to go.
About the author
Doug currently leads the ISG Cybersecurity unit and offers expertise in cybersecurity strategy, large scale transformation projects, infrastructure, Digital enablement, relationship management, and service delivery. Clients benefit from Doug's expertise from years of working with global clients within the life sciences, automotive manufacturing, aerospace, banking, insurance, financial services, healthcare, utilities and retail industries, as well as his deep and current knowledge of the service provider market. Doug routinely performs Strategy and Assessment engagements to assist clients in understanding how to select the optimal organizational and operational models to meet their business needs while minimizing security exposure and risk of loss.
LinkedIn Profile
