ISG Provider Lens™ Research (Archetype & Quadrant) are dedicated studies of relevant offerings related to specific IT or BPO topics or service lines over multiple regions (see “IPL Project Plan” for details). Leading vendors and service providers are evaluated and positioned, based on a transparent methodology.
The studies provide IT vendors and providers an informed base of data and research to enable them to compare their own offerings with those of relevant competitors and to reveal strengths and weaknesses as well as competitive differentiators and unique selling points. Our study serves as an important decision-making basis for positioning, key relationships, and go-to-market considerations. ISG Advisors and enterprise clients also leverage information from these reports in evaluating their current vendor relationships and potential new engagements.
Vendor positioning is based on a neutral and independent research and evaluation process. Participation in the study is FREE OF CHARGE. Vendors can purchase reprint rights of the study for marketing, press and sales purposes only AFTER the study has been completed.
A project brochure with further information can be obtained by clicking on the following graphic:

Definition of Quadrants (market categories)
As part of the ISG Provider LensTM Quadrant Study, we are introducing the following 8 quadrants on Cyber Security Solutions & Services.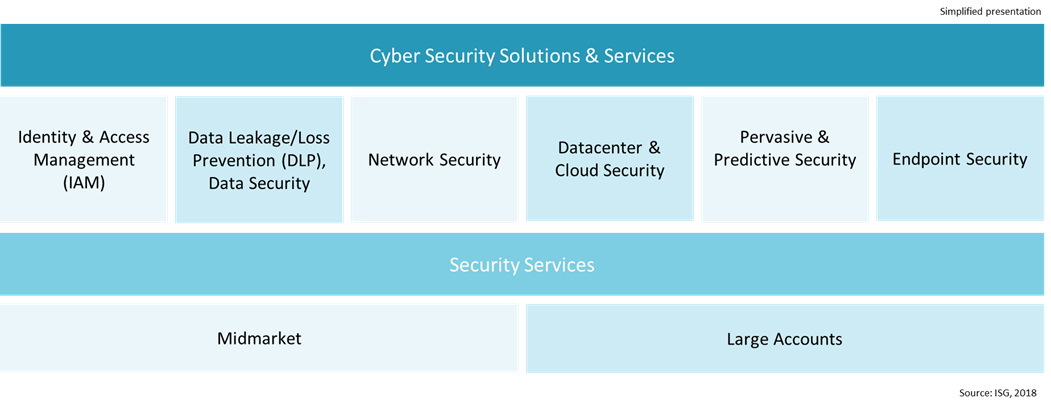
Segments Description
Identity & Access Management (IAM)
Identity & access management (IAM) products are used to collect, record and administrate user identities and related access rights. They ensure that access rights are granted, based on defined policies. To handle existing and new application requirements, security providers are increasingly challenged to embed mechanisms, frameworks and automation, e.g., risk analyses, into their management suites to provide real-time user and attack profiling functionality. Additional requirements are related to social media and mobile users to address clients’ security needs that go beyond traditional web- and context-related rights management. Includes cloud services (software as a service) by product providers, based on own software.
Data Leakage/Loss Prevention (DLP), Data Security
Data leakage/loss prevention (DLP) refers to products for the identification and monitoring of sensitive data to ensure that they can only be accessed by authorized users and to prevent data leakage. DLP products are gaining importance, since it becomes increasingly difficult for companies to control data movements and data transfers. The number of (mobile) devices within companies that can be used to store data is increasing; these devices are mostly equipped with their own Internet connection and can send and receive data without using the central Internet gateway. Devices also are supplied with a multitude of interfaces (e.g., USB, Bluetooth, WLAN, NFC), which can also be used to share data. Includes cloud services (software as a service) by product providers, based on own software.
Network Security
Enterprise networks are exposed to all kinds of attacks, from unauthorized access to computers by external parties to attacks attempting to interrupt the company's services (DoS/DDoS) and risks related to carelessness of the company's own employees. If a company is "worth" the trouble, attackers are increasingly investing great efforts and use highly sophisticated means to intrude deeply into the network infrastructure and use such cyber attacks (advanced persistent threats) to spy out sensitive data over a longer period of time without being detected.
Network security products have been designed to address these risks. Within the context of this study, network security is defined as measures to protect physical network infrastructures, including wireless LANs. Includes cloud services (software as a service) by product providers, based on own software.
Datacenter & Cloud Security
The datacenter & cloud security category comprises products to defend against IT infrastructure attacks or threats – independent of whether they are installed in the cloud (private, public, hybrid or multi-cloud) or on-premise. Includes cloud services (software as a service) by product providers, based on own software.
Pervasive & Predictive Security
Pervasive & predictive security products deal with pervasive, comprehensive protection. Predictive security has its origins in the network security arena, and the combination of both disciplines has caused a change of paradigms towards comprehensive security products, consisting of an overall set of enterprise-wide security technologies, combined with the ability to secure identities and data across the whole range of products, make predictions on and assess the risks of new technologies and services and their delivery. Includes cloud services (software as a service) by product providers, based on own software.
Endpoint Security
Endpoint security products can be used to ensure the security of clients and their interfaces within the network. Mobile security as a part of endpoint security refers to the protection of mobile processes, applications and devices (such as smartphones, tablets, laptops) and connecting networks against threats and vulnerabilities. Includes cloud services (software as a service) by product providers, based on own software.
Security Services
Security services cover services for security solutions. Services include consulting, training, integration, maintenance, support or management security services. Managed security services comprise the operations and management of an IT security infrastructure for one or several customers by a security operations center. The midmarket target group comprises companies with at least 50 up to 4,999 employees. The large accounts target group comprises companies with at least 5,000 employees. This analysis examines services that do not have an exclusive focus on the respective provider’s own proprietary products. Includes cloud services (software as a service) by providers that are not product providers.
